C2IT Blog
News, Resources & Links
Welcome to our blog. This is a place where we share our thoughts as well as links to great articles we hope you’ll find useful.
If you’d like to see us write about something specific, please feel free to fill out our contact form. Select Blog Suggestion from the dropdown menu.
C2IT’s Sixth Annual Pumpkin Decorating Contest
2024 marked C2IT's sixth year doing a pumpkin painting contest among the staff. This is an event everyone looks forward to each year. With several new staff additions this year, the competition was particularly fierce. Everyone brought their A game, but only three...
8 Tips for Safeguarding Your Gadgets While Traveling
Traveling with technology has become a necessity. Whether for work, communication, or entertainment, we rely heavily on our devices. But traveling exposes these gadgets to various risks. Theft, damage, and loss are common concerns. We’ve put together some helpful tips...
Streamlining Success – A Guide to Task Automation for Small Enterprises
Running a small business is a whirlwind. You juggle a million tasks and wear countless hats. You also constantly fight the clock. What if you could reclaim some of that precious time? Enter task automation. It’s your secret weapon for streamlining your workflow and...
I Got Scammed! How Did I Know and How Did I Fix It?
Last week, I willingly gave my name, address, phone number, and debit card info to a fraudulent website. You might think that someone like me would be immune to these types of mistakes. After all, I work for an IT company. I help educate people about their online...
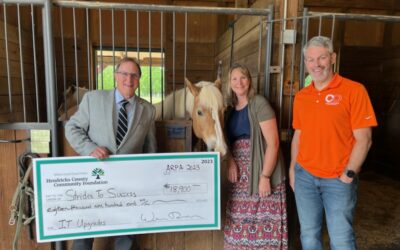
Client Spotlight – Strides to Success
Over the past 20 years, C2IT has been honored to partner with some incredible clients to help them leverage their technology to achieve their goals. In early 2024, we were approached with an incredible opportunity to partner with a local non-profit called Strides to...
Plainfield Chamber Golf Outing Recap 2024
While this year's Plainfield Chamber Golf Outing at Deer Creek Golf Club in Clayton was bookended by storms, our team weathered the conditions and represented C2IT well both at our tent and on the golf course as players. Much of our team took shifts helping out at...
Employee Spotlight – Jonathan Chase
We are excited to shine the employee spotlight on Jonathan Chase, our new Development & Operations Engineer who’s already making a significant impact. I got the chance to interview him and dive into some of his experiences and insights so far at C2IT, and I’m...
Phishing 2.0: How AI is Amplifying the Danger and What You Can Do
Phishing has always been a threat. Now, with AI, it's more dangerous than ever. Phishing 2.0 is here. It’s smarter, more convincing, and harder to detect. Understanding this new threat is crucial. A recent study found a 60% increase in AI-driven phishing attacks. This...
Is Your Business Losing Money Because Employees Can’t Use Tech?
Shiny new tech can be exciting! It promises increased efficiency, happier employees, and a competitive edge. It’s also necessary to stay competitive in today’s technology-driven business world. But that promise can turn into a financial nightmare if you neglect two...
Employee Spotlight – Ben Laver
Introducing Ben Laver: Enhancing Our Team at C2IT Consulting At C2IT Consulting, we're excited to welcome Ben Laver as our newest IT Support Technician. Ben’s journey to our team is a story of dedication, community ties, and a passion for technology that perfectly...
Employee Spotlight – Jill Parker
For 20 years, C2IT has been helping small businesses achieve their goals. After many years of this, we have grown to the point of needing help too, specifically in administration. Acknowledging this need, we sought out an expert in office management and landed a star....
Summer Reading: E-Readers and Apps for Enjoying Books on the Go
As summer arrives with its promise of sunny days and leisurely afternoons, many of us look forward to diving into a good book. Whether you're lounging at the Mooresville Pool, relaxing in Pioneer Park, or enjoying a backyard hammock, reading is a perfect way to...
What Were the Coolest Consumer Products Showcased at CES 2024?
The annual Consumer Electronics Show (CES) was an exciting one this year. It left us with a mind-blowing glimpse into the future of technology. CES 2024 showcased a smorgasbord of cutting-edge gadgets. Including transparent TVs and robot pet buddies. These gadgets...
Why Do I Keep Seeing All These Ads? The Basics of Digital Marketing
Have you ever wondered why the internet seems to know exactly what you're thinking? Maybe you've been eyeing a new pair of shoes, and suddenly, you start seeing ads for them everywhere online. This is not a coincidence—it's digital marketing at work. What is...
Employee Spotlight – Isaiah Zeller
2024 marks the 20th anniversary for C2IT Consulting. For 20 years, we've been helping small businesses maximize their technology to achieve their goals. From the beginning, C2IT has been helping businesses with their websites, their daily support, IT infrastructure,...
Employee Spotlight – Matthew Moxley
C2IT Consulting is committed to investing in young people who are exploring careers in the realm of technology. We have been blessed over the years with some great interns and residents who have made a great impact on our team and helped our clients in creative ways....
Smart Tips for Building a Smart Home on a Budget
Imagine a world where your lights turn on automatically as you walk in the door. Your coffee starts brewing before you even crawl out of bed. A simple voice command adjusts the temperature to your perfect setting. This is no longer just something out of a sci-fi...
Guide to Improving Your Company’s Data Management
Data is the lifeblood of modern businesses. It fuels insights, drives decision-making, and ultimately shapes your company's success. But in today's information age, data can quickly become overwhelming. Scattered spreadsheets, siloed databases, and inconsistent...
Don’t Risk It! Why You Shouldn’t Skip Vulnerability Assessments
Cyber threats are a perpetual reality for business owners. Hackers are constantly innovating. They devise new ways to exploit vulnerabilities in computer systems and networks. For businesses of all sizes, a proactive approach to cybersecurity is essential. One of the...
7 Common Pitfalls When Adopting Zero Trust Security
Zero Trust security is rapidly transforming the cybersecurity landscape. It moves away from traditional perimeter-based security models. In this approach, every connection attempt is continuously verified before granting resource access. 56% of global organizations...
4 Ways Small Businesses Can Leverage Copilot for Microsoft 365
What are some of the key differentiators that can propel small businesses forward? They include efficiency, productivity, and innovation. Microsoft has expanded the availability of one of its most dynamic tools to SMBs. A tool that can be a real game-changer for...
Introducing the New Microsoft Planner (Everything You Need to Know)
Calendars, task lists, and project planning are important business tools. Many people use Microsoft’s apps to power these processes including Planner, Microsoft To Do, and Project for the web. These tools help keep processes on track and enable task accountability....
How to Properly Deploy IoT on a Business Network
The Internet of Things (IoT) is no longer a futuristic concept. It's rapidly transforming industries and reshaping how businesses operate. IoT is a blanket term to describe smart devices that are internet enabled. One example is smart sensors monitoring production...
Here Are 5 Data Security Trends to Prepare for in 2024
With cyber threats evolving at an alarming pace, staying ahead of the curve is crucial. It’s a must for safeguarding sensitive information. Data security threats are becoming more sophisticated and prevalent. The landscape must change to keep up. In 2024, we can...